Introduction to Security Roles and Privileges.
Role-based security model is hierarchical, and each element in the hierarchy represents a different level of detail. Permissions represent access to individual securable objects, such as menu items to forms, reports and class. Privileges are composed of permissions and represent access to tasks, such as creating a record, editing it or deleting it. Roles are a collection of privileges which are a part of a particular activity. Role names can be compared to the role of an employee who performs a particular task in an organization.
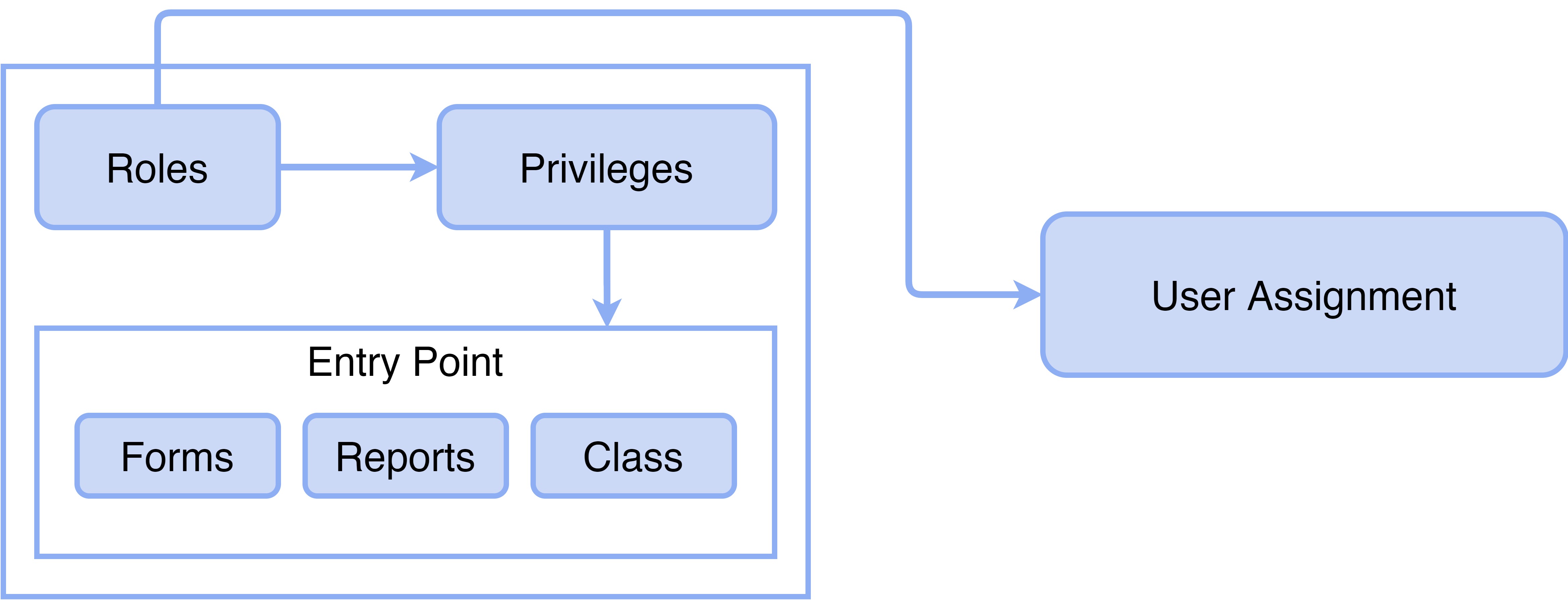
Security Roles and Privileges flow chart
Security roles.
All users must be assigned to at least one security role in order to have access to Boon ERP. The security roles that are assigned to a user determine the duties that the user can perform and the parts of the user interface that the user can view.
Security Privileges.
In the security model, a privilege specifies the level of access that is required to perform a job, solve a problem, or complete an assignment. Privileges can be assigned directly to roles. This is so that the privileges are first grouped together into a roles, which makes it easier maintenance.
Permissions.
Each function, such as a form, report or class, is accessed through an entry point. Menu items, are referred to collectively as entry points. Users are assigned with roles so that the right permissions can be obtained to all.